Application Architecture & Product-Level Security
To ensure maximum security, we have segregated the deployment architecture into three layers:
- The Elastic Load Balancer: We will use an Elastic Load Balancer (ELB) in front of Application layer so all requests coming to the application will first hit the Elastic Load Balancer and then will go to Webserver/Application layer.
- Application/Webserver Layer
- Database Layer: All databases will reside in its own private subnet, so no direct internet will be accessible from the DB subnet group.
Multi-factor Authentication (MFA)
For all Amazon Web Service (AWS) console users MFA will be enforced as per our security policies.
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of the usual user name and password. With MFA enabled, when a user signs in to an AWS website, they will be prompted for their user name and password (the first factor—what they know), as well as for an authentication code from their AWS MFA device (the second factor—what they have). Taken together, these multiple factors provide increased security for your AWS account settings and resources.
MFA will be enabled for the AWS account and for individual Identity and Access Management (IAM) users that have access to the AWS account. MFA will also be used to control access to AWS service APIs.
No Direct Internet Connection to DB Server from Internet
All Databases servers/ farm can be accessed only from whitelisted IP. Only specific ports will be opened from security group of Application/Webserver security group.
Identity And Access Management (IAM)
AWS Identity and Access Management (IAM) is a web service that will securely control access to AWS resources for the admin users. IAM will be used to control the access to the AWS resources (authentication) and to define usage rights (authorization).
IAM Features
IAM provides the following features:
- Granular Permissions: Different permissions can be granted to different people for different resources. For example, a user might be allowed complete access to Amazon Elastic Compute Cloud (Amazon EC2), Amazon Simple Storage Service (Amazon S3), Amazon SES, and other AWS services. Another user will be allowed only read-only access to just some S3 buckets, or permission to administer just some EC2 instances.
- Secure Access to AWS Resources: IAM features will be used to securely give applications that run on EC2 instances the credentials that they need in order to access other AWS resources, like S3 buckets and RDS or SES service.
- Identity Federation: Temporary access can be granted to users of the corporate network who already have passwords elsewhere.
- Identity Information for Assurance: Log records which contain information about users who made requests for resources will be tracked through AWS CloudTrail. This information is based on IAM identities.
- PCI DSS Compliance: IAM supports the processing, storage, and transmission of credit card data by a merchant or service provider, and has been validated as being compliant with Payment Card Industry (PCI) Data Security Standard (DSS).
Access to Talentpool Administrator
Resource access of the instances inside the VPC to the ones outside the VPC can be controlled.
The default VPC includes an Internet gateway, and each default subnet is a public subnet. Each instance that you launch into a default subnet has a private IP address and a public IP address. These instances can communicate with the Internet through the Internet gateway. An Internet gateway enables your instances to connect to the Internet through the Amazon EC2 network edge.
Audit Trail Via CloudTrail
AWS CloudTrail is a web service that records AWS API calls for the account and delivers log files to a specified ID. The recorded information includes the identity of the API caller, the time of the API call, the source IP address of the API caller, the request parameters, and the response elements returned by the AWS service.
With CloudTrail, you can get a history of AWS API calls for your account, including API calls made via the AWS Management Console, AWS SDKs, command line tools, and higher-level AWS services (such as AWS CloudFormation). The AWS API call history produced by CloudTrail enables security analysis, resource change tracking, and compliance auditing.
AWS Deployment Diagram
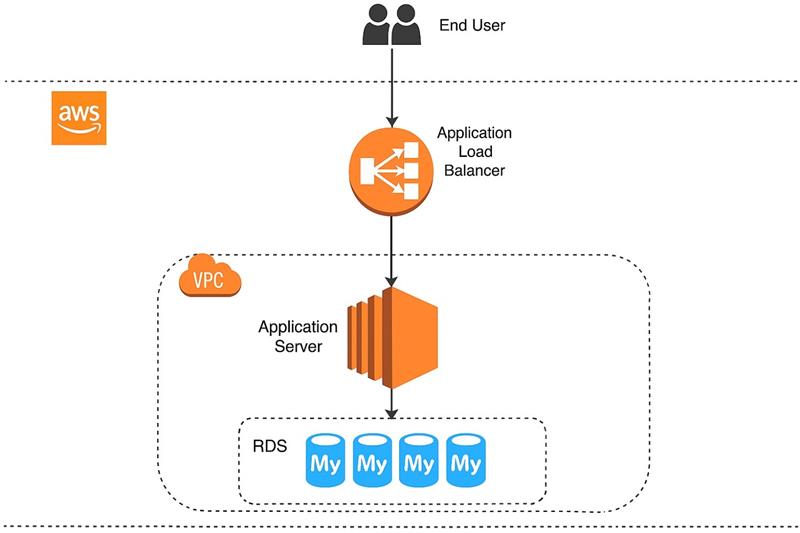
Talentpool's secure AWS deployment architecture showing the three-layer security model
Infrastructure Security Across Hosting Environments
- Resilient Cloud Infrastructure: A backup data center on AWS ensures business continuity and disaster recovery. Production systems are monitored for uptime, load, and anomalies in real time.
- OWASP Compliance: Talentpool incorporates guidance from OWASP (Open Web Application Security Project) that identifies the most critical web application security flaws and defines best practices for developing secure web applications. Its design ensures protection from attacks such as SQL Injection, Cross-site Scripting (XSS), Blind XPATH Injection, Cross Site Request Forgery (CSRF) and Cache Poisoning.
- Encryption: Talentpool supports deployment using HTTPS to create secure channel for data and protects it against eavesdroppers and man-in-the-middle attacks. This is particularly useful for multi- location organizations that require Talentpool to be accessed over the internet. Sensitive information such as passwords are always transmitted in an encrypted form.
- Login & Password Security: Talentpool limits access to all parts of the application through logins and passwords. Passwords are hashed and never travel across the network without encryption. The time stamp and IP address of the last login is displayed each time a user logs in so that any misuse can be proactively detected by the users themselves.
- Role Based Access Control: Talentpool supports role-based authorization, which means that users have limited access to data and functionality. The administrator can define an unlimited number of roles and control access to the application at a screen, action, data or candidate level.
- Session Security: User sessions are timed out after a specified period of inactivity.
- Secure Cookies: Talentpool uses secure cookies with a maximum 24-hour lifespan for a logged-in user. This cookie is cleared while invalidating the session.
